Ruby for Pentesters(or Pentesting for Rubyists)
Hello everyone! A couple of weeks ago, I gave a talk at the OWASP Kyiv Chapter Kick-off meetup, and this article provides an overview of my presentation. Here, you will find a concise list of the tools, services, suggestions, and comments I covered in the talk. I hope you find this article informative and valuable. Thank you!
The presentation itself can be found at: slideshare.net/owaspKyiv.
OWASP?
OWASP is “an open community dedicated to enabling organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted.” In short, OWASP is a worldwide non-profit organization that wants to improve software security.
OWASP Kyiv?
The OWASP Chapters program helps to enhance local discussion of application security worldwide.OWASP Kyiv chapter was founded in 2017 by Vlad Styran and Ihor Bliumental. The chapter is run by a team of dedicated cybersecurity enthusiasts: Kyrylo Hobrenyak, Dmytro Diordiychuk, Anatolii Bereziuk and Serhii Korolenko.
The chapter aims at holding quarterly meetups in the format of 2 practical workshops and up to 5 talks. The meetups are normally streamed online and recorded, and are followed by unofficial parties in Kyiv pubs.
If interested, please send your talk submissions using the OWASP Ukraine CFP page.
Why Ruby?
As a former Ruby/JS programmer, I believe that Ruby has limitless potential for automating daily rutines and security audits, just like other popular languages such as Python and PHP. Ruby code is easy to comprehend and maintain as it "is written for humans by humans” =) It is an elegant and expressive language.
Apps and scripts written on Ruby can be extended using native C libraries, existing C-based tools, or even bridged with other languages like Java. For instance, JRuby, a 100% Java implementation of Ruby, can be easily integrated with the BurpSuit for better automation.
Furthermore, the Ruby community is vast, welcoming, and always willing to assist with any issues you may encounter.
Tools overview.
As someone who transitioned from Ruby development into infosec, I find it fascinating to see the abundance of widely-used tools written in Ruby. In the next section of this blog post, I will provide a brief list of some of these tools:
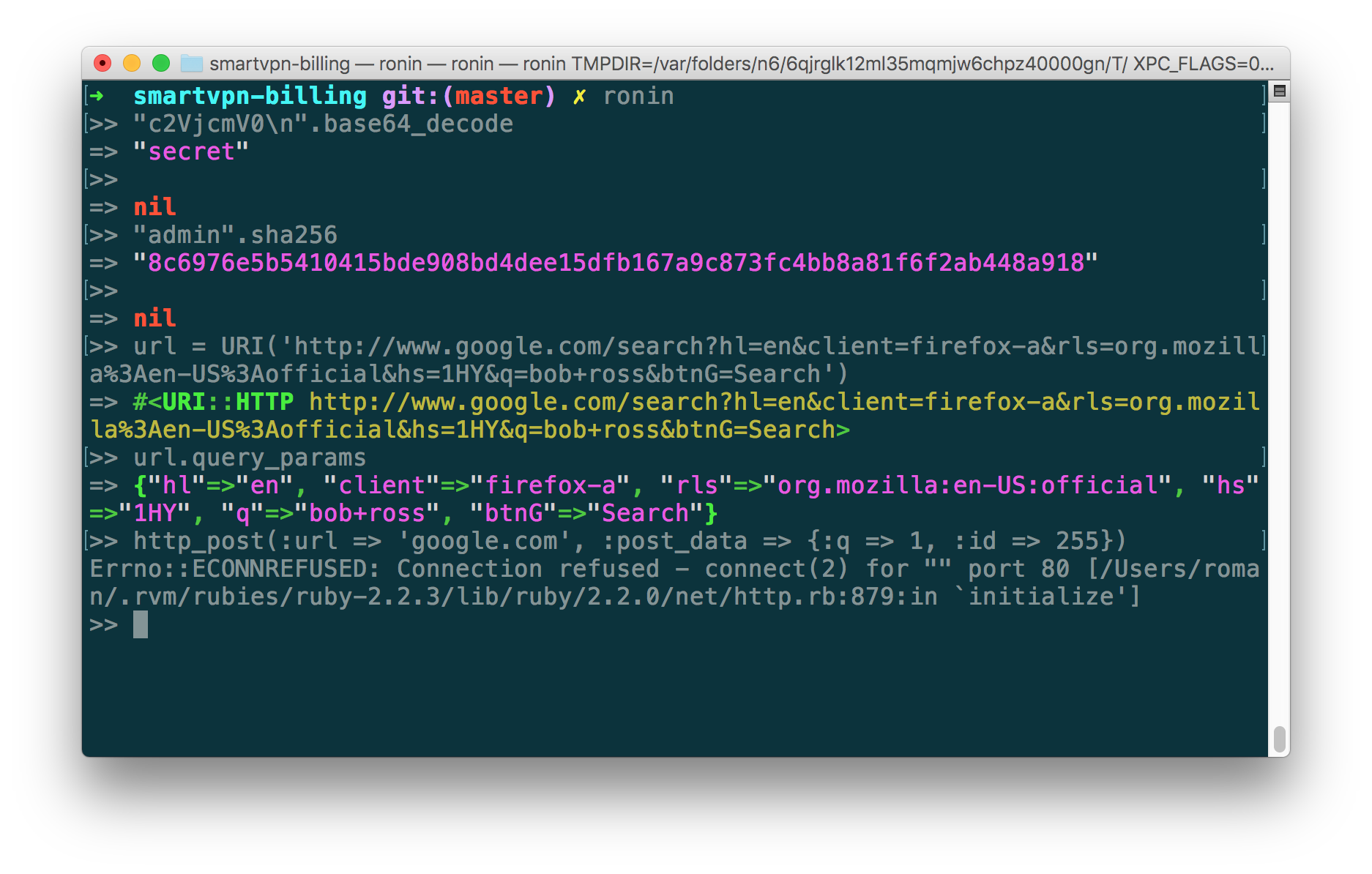
1. Ronin
Website: https://ronin-rb.dev
GitHub: https://github.com/ronin-rb/ronin
Ronin is a free and Open Source Ruby toolkit for security research and development. Ronin contains many different CLI commands and Ruby libraries for a variety of security tasks, such as encoding/decoding data, filter IPs/hosts/URLs, querying ASNs, querying DNS, HTTP, scanning for web vulnerabilities, spidering websites, install 3rd party repositories of exploits and/or payloads, run exploits, write new exploits, managing local databases, fuzzing data, and much more.
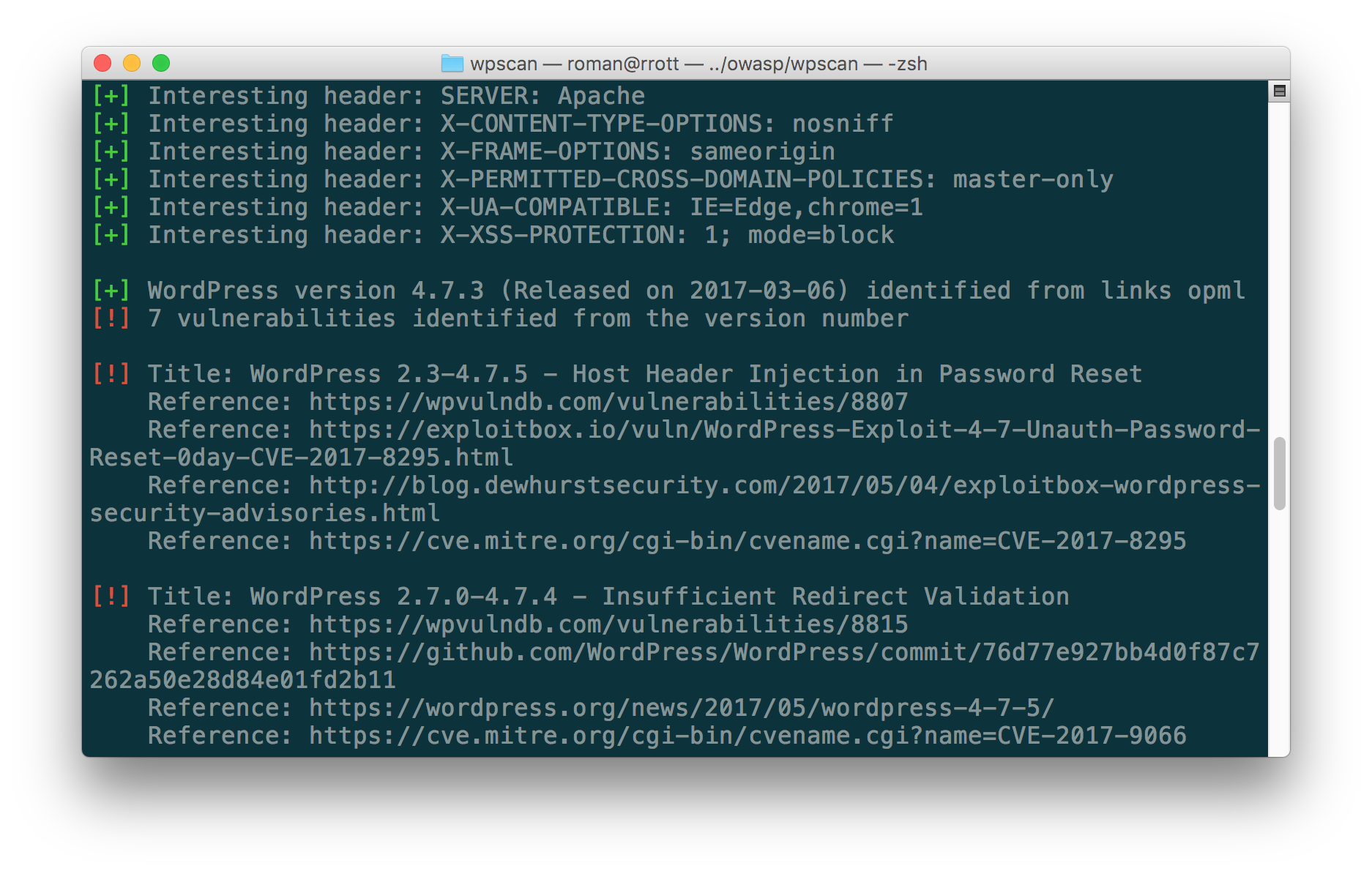
2. WPScan
Website: https://wpscan.org
GitHub: https://github.com/wpscanteam/wpscan
The WPScan tool is a free black box WordPress security scanner. It can scan and enumerate plugins that are installed, provide links to CVEs, shows hints, dangers and a lot of other info. The WPScan CLI tool uses a database of 38,496 WordPress vulnerabilities.
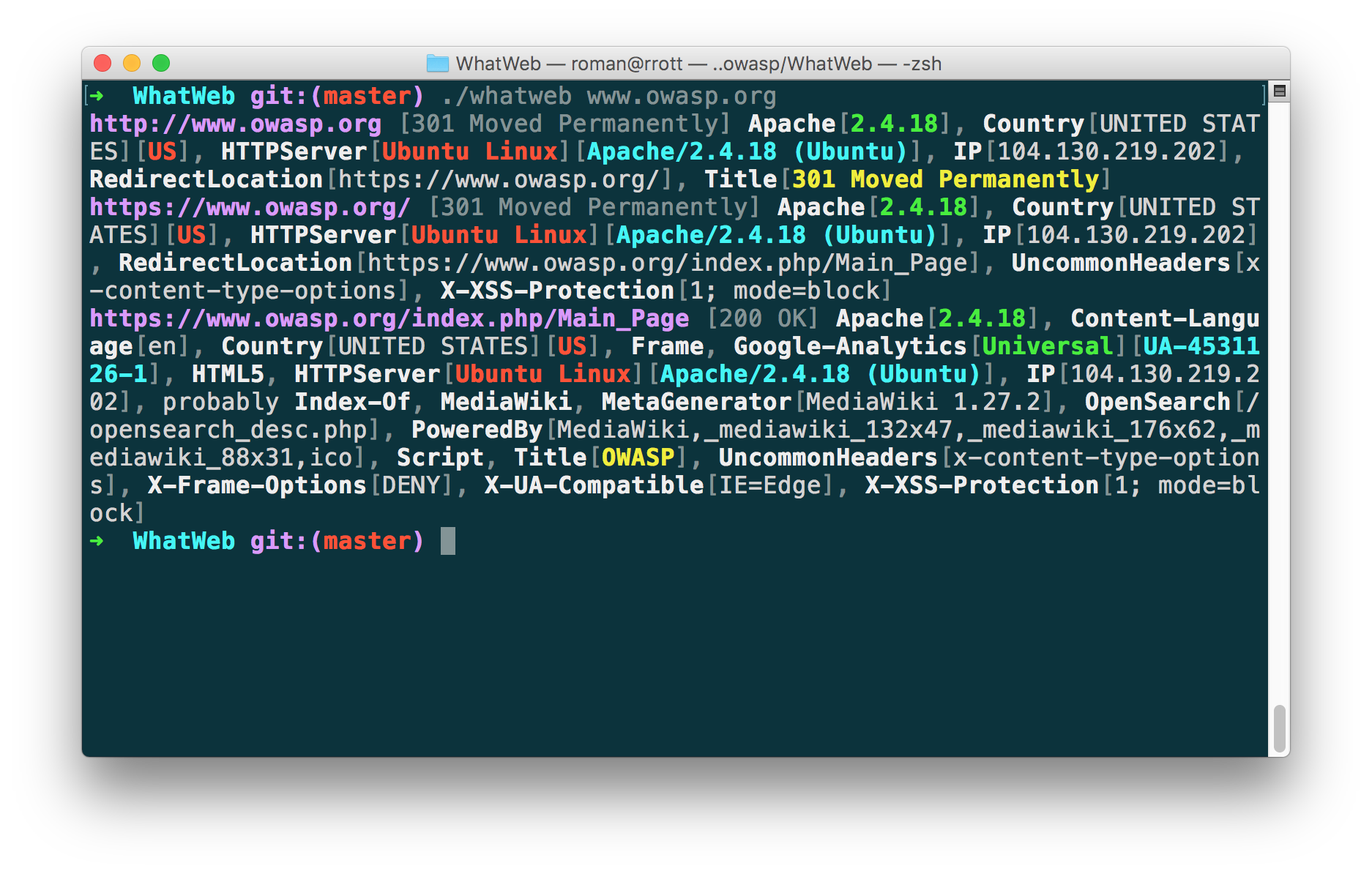
3. WhatWeb
Website: https://www.morningstarsecurity.com/research/whatweb
GitHub: https://github.com/urbanadventurer/WhatWeb
WhatWeb recognizes web technologies including CMS, blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. It has about 2K plugins, each to recognize something different. It also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.
Notes as for 2023: Latest Release is v0.5.5. January 16, 2021
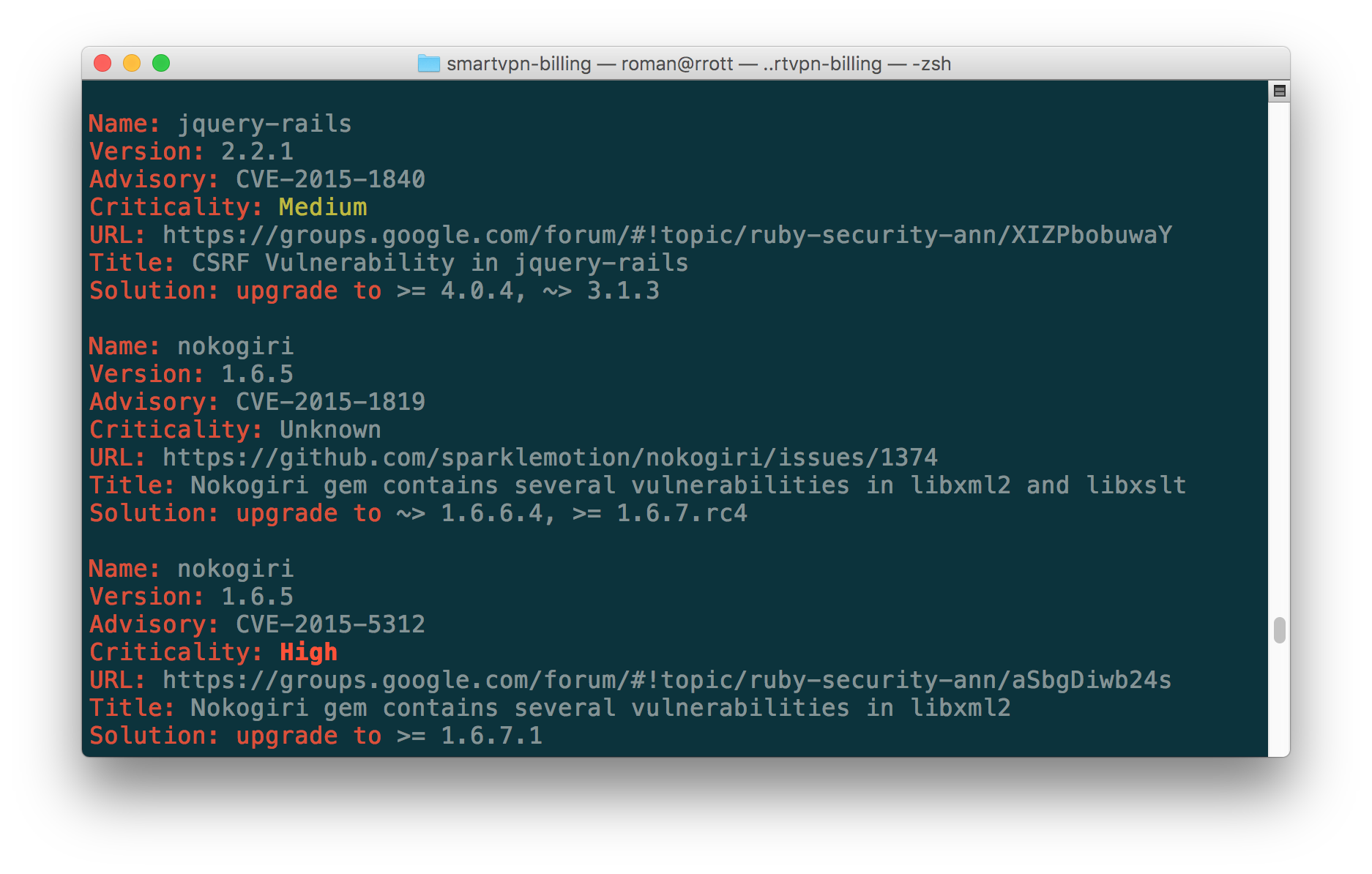
4. bundle-audit
GitHub: https://github.com/rubysec/bundler-audit
It’s a patch-level verification for Bundler. bundle-audit checks for vulnerable versions of gems in Gemfile.lock, prints advisory information and can be useful for testing Ruby-based apps in case you have its source code(or just Gemfile.lock)
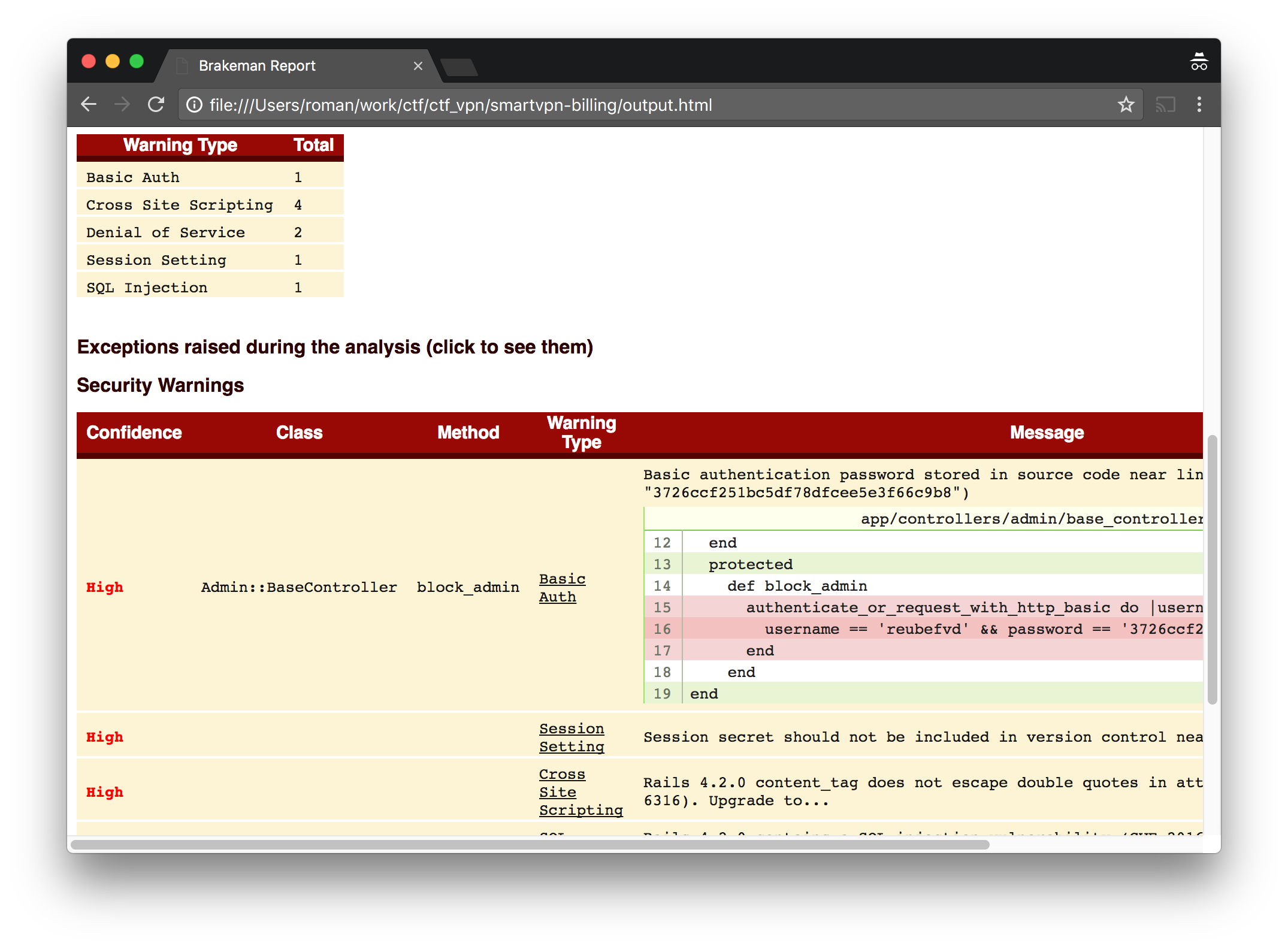
5. Brakeman
Website: http://brakemanscanner.org
GitHub: https://github.com/presidentbeef/brakeman
Brakeman is a static analysis tool which checks Ruby on Rails applications for security vulnerabilities. As the previous one, it can be useful in case of open-box testing when you have access to the apps’ source. It generates a list of potential(and sometimes real) problems and saves them into an HTML file with a detailed description.
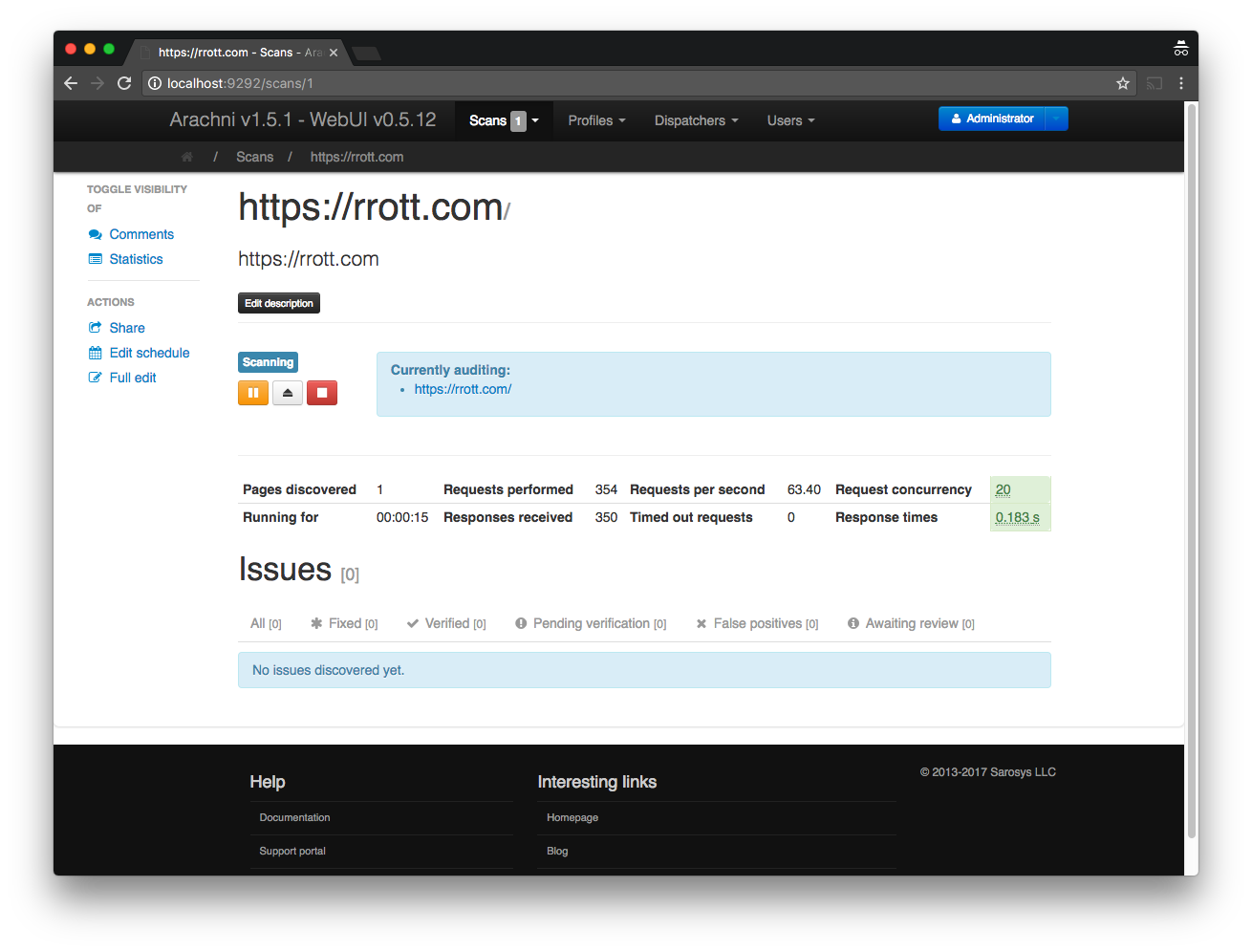
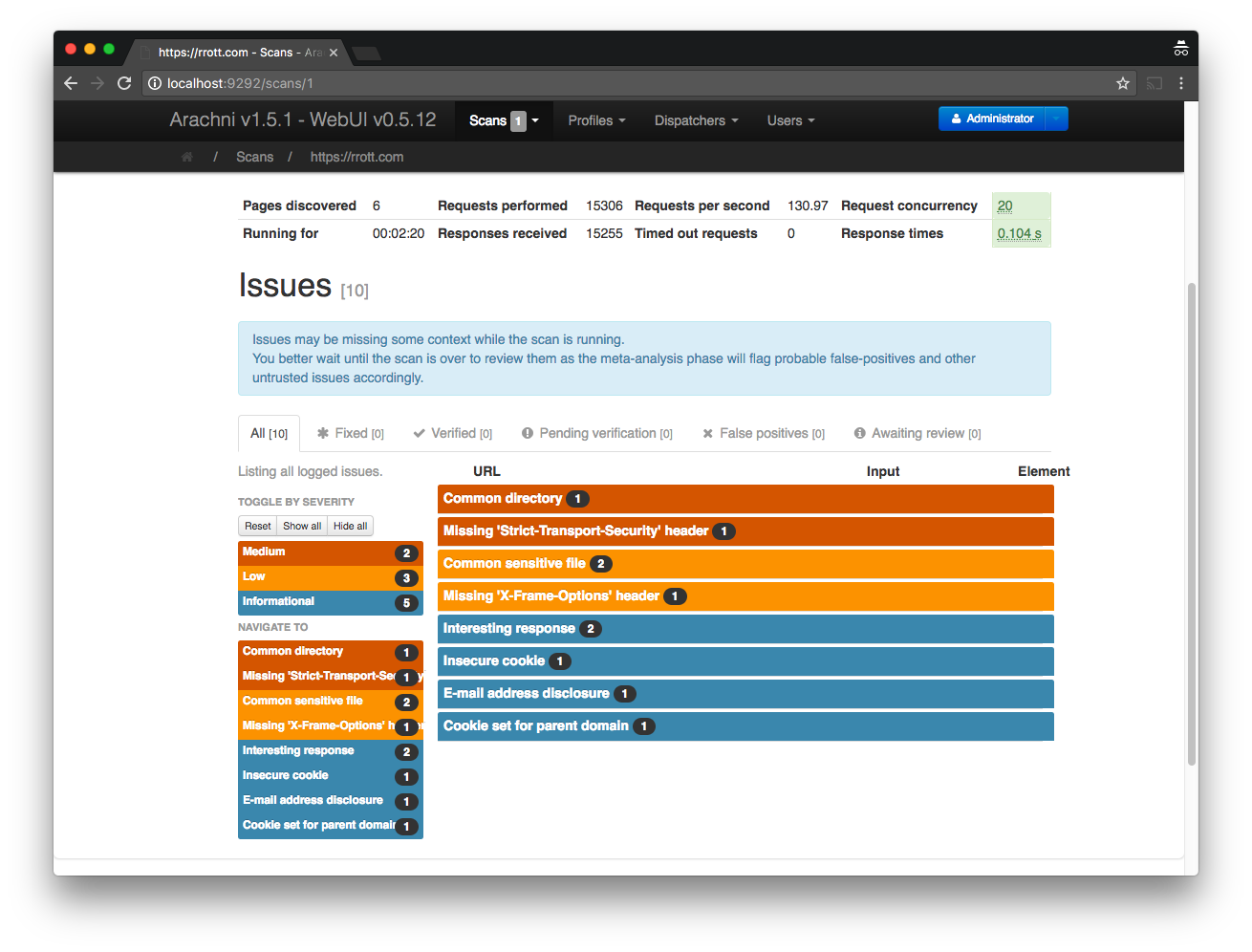
6. Arachni
Website: http://www.arachni-scanner.com
GitHub: https://github.com/Arachni/arachni
Arachni is a modular Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web apps. It can be used by a team of testers with different roles, test cases, subjects and all the results can be managed by admins.
Notes as for 2023: Arachni is heading towards obsolescence, try out its next-gen successor “Ecsypno SCNR”
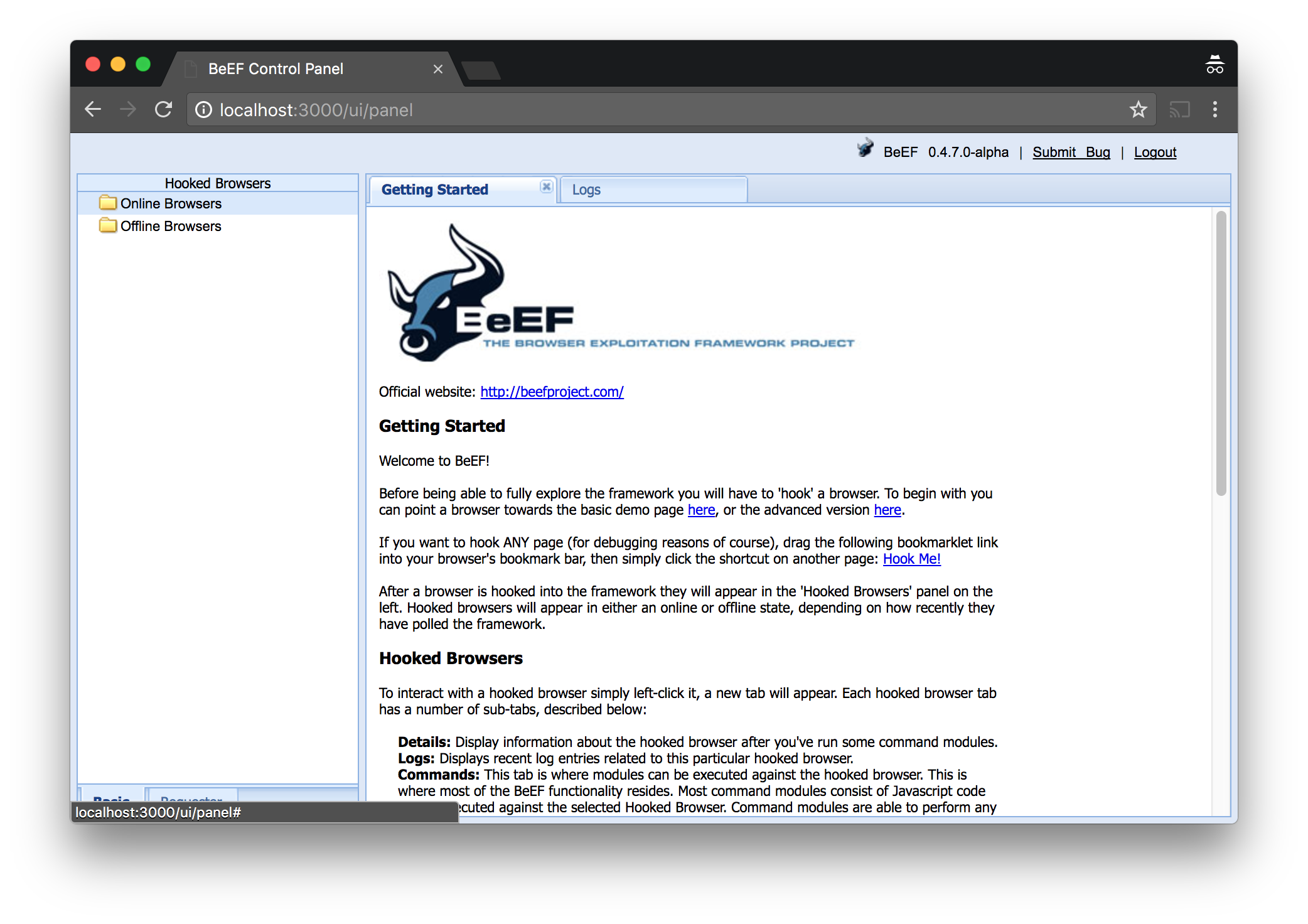
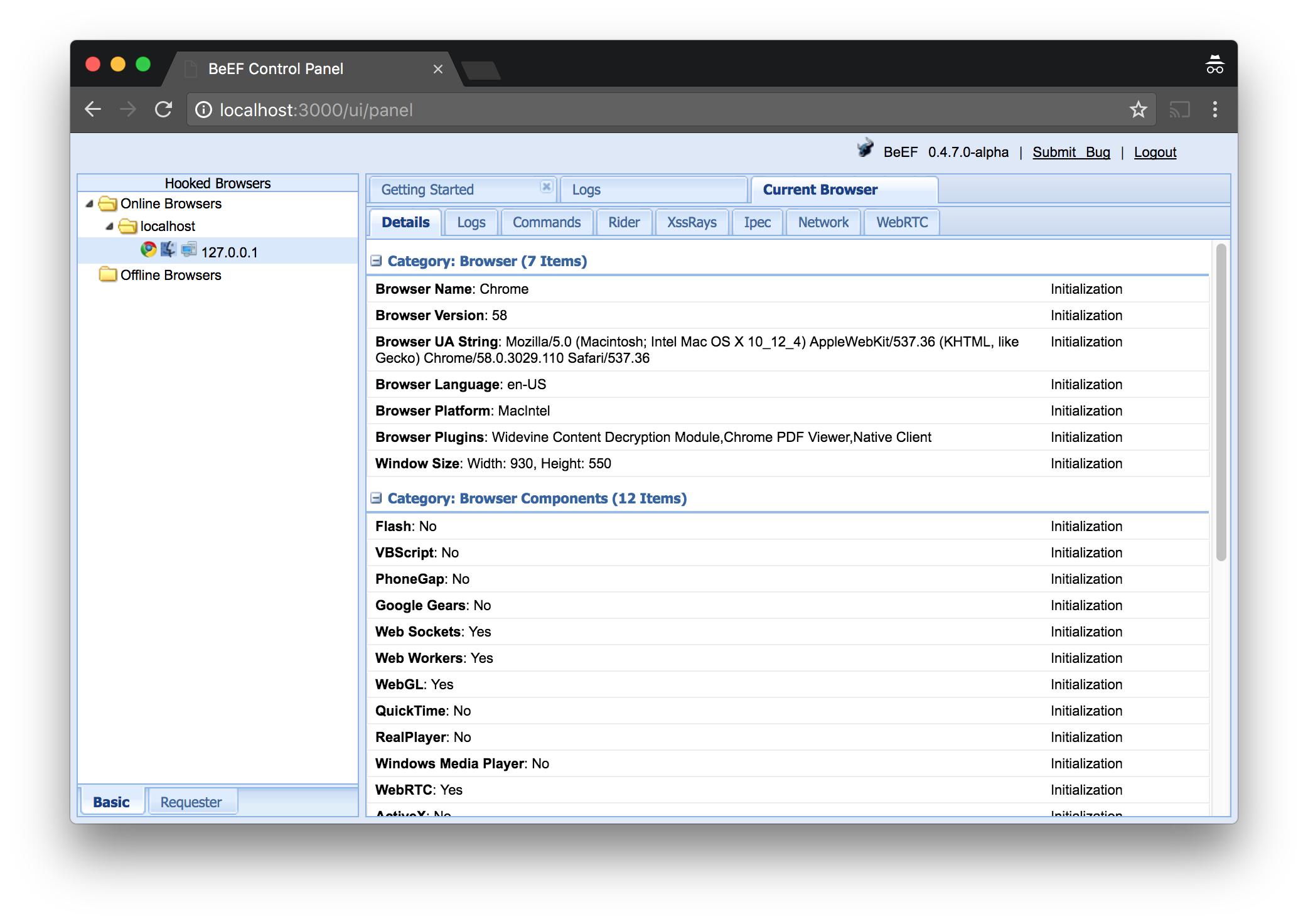
7. BeEF
Website: http://beefproject.com
GitHub: https://github.com/beefproject/beef
BeEF is short for The Browser Exploitation Framework - it is a penetration testing tool that focuses on the web browser. “BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.”
8. Metasploit
Website: https://www.metasploit.com
World’s most used penetration testing software. Nothing to say there - everybody in infosec knows it, and yes, it is written using Ruby =)
Scripted Pen-Testing, Automatization
In Ruby, it’s a common practice to utilize the message-object protocol since almost everything is an object in this language. You might say that Ruby is a “message-oriented” language, where objects contain other objects and “communicate” with each other by reacting to messages.
For instance, you can write a script to retrieve an entire website, parse and store its web pages as Ruby objects using various Ruby parsers, analyze this data using other gems or your own code, open some “interesting” pages in a headless browser, inject and submit payloads, save screenshots in PDF format with detailed information about the payloads, affected page, and steps for manual analysis, all in one script and all in the background. It’s truly amazing, isn’t it?
You may find next gems pretty interesting:
- Oga - XML/HTML parser
- html-pipeline - GitHub HTML processing filters and utilities. This module includes a small framework for defining DOM based content filters and applying them to user provided content.
- Happymapper allows you to parse XML data and convert it quickly and easily into ruby data structures.
- nokogiri - is a Rubygem providing HTML, XML, SAX, and Reader parsers with XPath and CSS selector support.
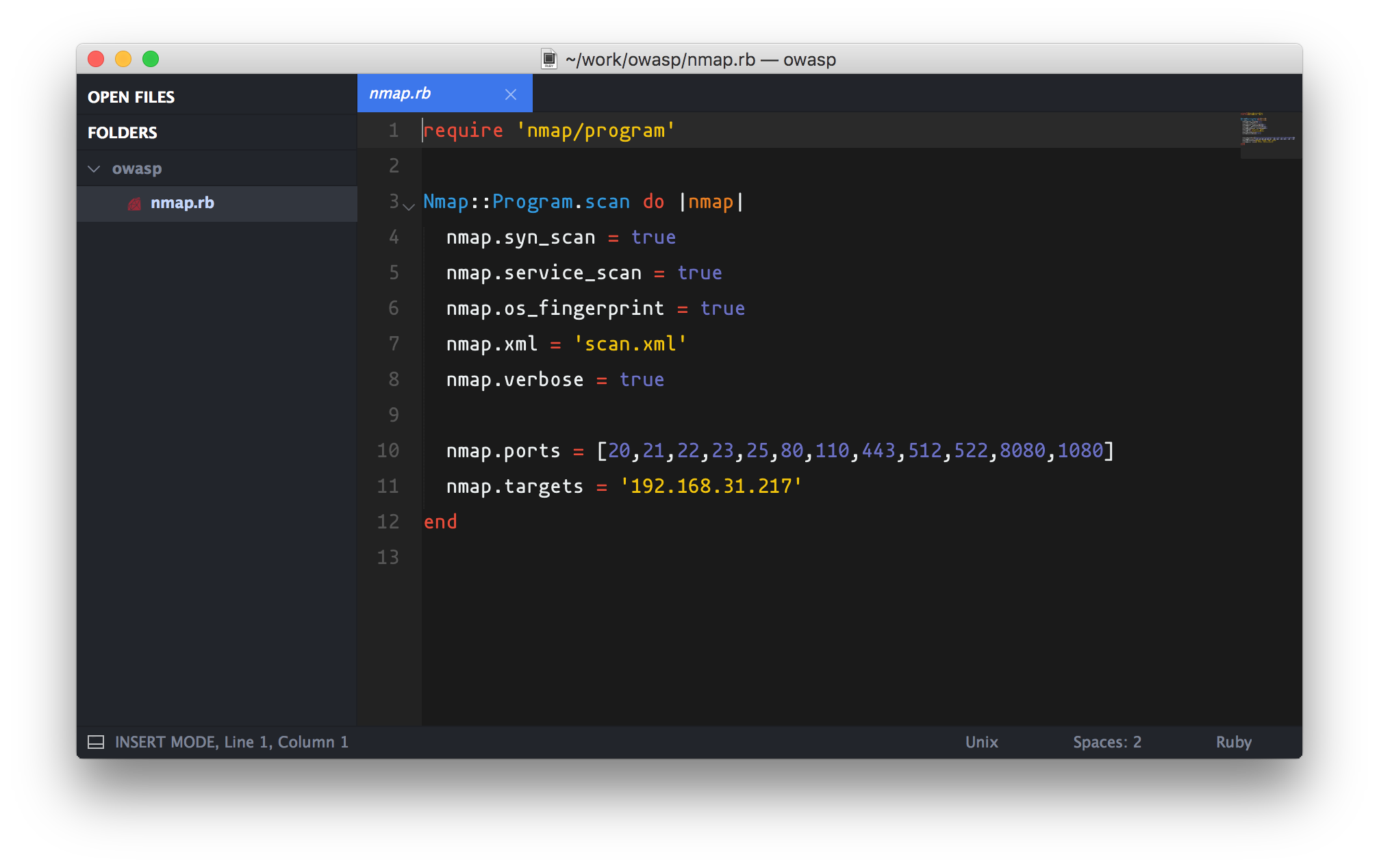
- ruby-nmap - a Ruby interface to nmap, the exploration tool and securit/port scanner.
- selenium - is for automating web applications for testing purposes, but is certainly not limited to just that ;)
- Watir - ruby library for automating tests. Watir interacts with a browser the same way people do: clicking links, filling out forms and validating text.
Recomendations
- I suggest reading “RubyFu, where Ruby goes evil!” book by @Rubyfu. This book is a collection of ideas, tricks, and skills that could be useful for Hackers.